
AttackIQ
Founded Year
2013Stage
Series C | AliveTotal Raised
$80.9MValuation
$0000Last Raised
$44M | 5 yrs agoMosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
-62 points in the past 30 days
About AttackIQ
AttackIQ offers breach and attack simulation products for security control validation within the cybersecurity industry. It emulates adversary tactics, techniques, and procedures, aligning with the MITRE ATT&CK framework, to provide insights into security program performance and offer data-driven analysis and mitigation guidance. Its solutions cater to sectors, including energy, financial services, healthcare, and federal organizations. It was founded in 2013 and is based in Los Altos, California.
Loading...
ESPs containing AttackIQ
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The breach & attack simulation (BAS) market provides solutions and platforms that simulate real-world cyber attacks and security breaches to assess the effectiveness of an organization's security defenses. Vendors in this market offer organizations a proactive approach to identifying and remediating cybersecurity gaps, reducing the risk of a breach. BAS solutions provide a holistic view of an orga…
AttackIQ named as Challenger among 15 other companies, including Fortinet, Pentera, and Rapid7.
Loading...
Research containing AttackIQ
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned AttackIQ in 1 CB Insights research brief, most recently on Jan 25, 2023.
Expert Collections containing AttackIQ
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
AttackIQ is included in 2 Expert Collections, including Regtech.
Regtech
1,611 items
Technology that addresses regulatory challenges and facilitates the delivery of compliance requirements. Regulatory technology helps companies and regulators address challenges ranging from compliance (e.g. AML/KYC) automation and improved risk management.
Cybersecurity
11,188 items
These companies protect organizations from digital threats.
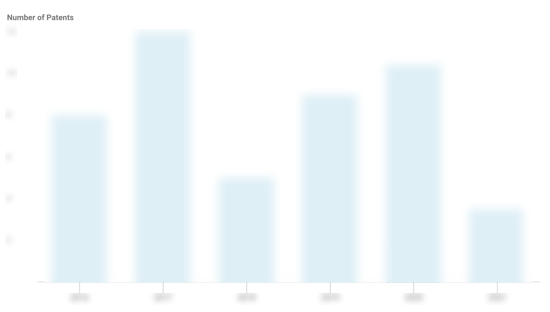
AttackIQ Patents
AttackIQ has filed 13 patents.
The 3 most popular patent topics include:
- computer security
- computer network security
- security technology
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
12/5/2023 | 12/24/2024 | Computer network security, Computer security, Security technology, Network protocols, Wireless networking | Grant |
Application Date | 12/5/2023 |
|---|---|
Grant Date | 12/24/2024 |
Title | |
Related Topics | Computer network security, Computer security, Security technology, Network protocols, Wireless networking |
Status | Grant |
Latest AttackIQ News
Nov 14, 2025
Emulating the Espionage-Oriented Group SideWinder SideWinder is a long-running threat actor active since at least 2012, primarily engaged in cyber-espionage. It has been observed targeting military and government entities, as well as ports and maritime facilities across the Indian Ocean and Mediterranean Sea, including Pakistan, Egypt, Sri Lanka, Bangladesh, Myanmar, Nepal and the Maldives. Initial access is typically obtained via spear-phishing emails containing malicious documents that mimic trusted organizations. These documents use a remote template injection technique (CVE-2017-0199) to retrieve an RTF that contains embedded shellcode exploiting CVE-2017-11882. The shellcode performs environment checks to detect virtualization or analysis systems; if the host is verified, it decodes and executes a small JavaScript payload fetched from a remote server. This payload connects to a malicious URL to retrieve additional malware stages or to exploit further vulnerabilities. The delivery infrastructure exhibits a level of sophistication aimed at evading detection and hindering analysis: geofencing returns an empty RTF to non-targeted requests, delivery and payload URLs are short-lived and routinely rotated (often unique per campaign or target set), and servers generate payloads on the fly so each download produces a file with a unique hash. These measures together reduce the usefulness of static indicators and increase the difficulty of sample correlation and analysis. The observed final payload, known as StealerBot, is a modular memory-resident backdoor designed for espionage. It operates entirely in memory, with decrypted components injected directly by the loader to avoid disk artifacts. AttackIQ has released a new attack graph that emulates the Tactics, Techniques, and Procedures (TTPs) associated with the deployment of SideWinder to help customers validate their security controls and their ability to defend against this threat. Validating your security program performance against these behaviors is vital in reducing risk. By using this new attack graph in the AttackIQ Security Optimization Platform, security teams will be able to: Evaluate security control performance against baseline behaviors associated with SideWinder Assess their security posture against a prolific and sophisticated adversary. Continuously validate detection and prevention pipelines against a threat that conducts espionage campaigns across multiple sectors and regions. Sidewinder – 2025-05 – Malicious Office Document Delivers StealerBot This emulation replicates the sequence of behaviors associated with the deployment of SideWinder on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress. Initial Access & Execution – Malware Delivery In this stage, a malicious Office document (.DOCX) is downloaded and saved to the system. Next, a Rich Text Format (.RTF) file is dropped and executed via mshta.exe. Finally, system memory is checked via GlobalMemoryStatusEx. 2025-05 SideWinder .DOCX Sample ( T1105 ): The SideWinder .DOCX Sample (SHA256: 57b9744b30903c7741e9966882815e1467be1115cbd6798ad4bfb3d334d3523d) is downloaded to memory and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples. 2025-02 SideWinder .RTF Sample ( T1105 ): The SideWinder .RTF Sample (SHA256: d9e373aeea5fe0c744f0de94fdd366b5b6da816209ac394cbbda1c64c03b50b1) is saved to disk to test endpoint controls and their ability to prevent the delivery of known malicious samples. Download and Execute Remote Payload with MSHTA ( T1218.005 ): This scenario downloads and executes a remote Microsoft HTML Application (HTA) from an AttackIQ controlled webserver, that contains embedded Visual Basic Script (VBS) code to create a canary file in the compromised file system. System Information Discovery via “GlobalMemoryStatusEx” Native API ( T1082 ): This scenario executes the GlobalMemoryStatusEx Windows API call to gather information about physical and virtual memory. Execution & Persistence – Malware Execution In this stage, the Windows Management Instrumentation Command-line (WMIC) is executed to retrieve the list of antivirus products installed on the system. Next, a payload is executed using pcalua.exe. Finally, persistence is established through either scheduled tasks or registry run keys as a fallback. Discover Security Software (AntiVirusProduct) using WMI Command ( T1518.001 ): This scenario uses a native Windows Management Instrumentation Command-line (WMIC) to determine which software has been installed as an AntiVirusProduct class. Indirect Command Execution using “pcalua.exe” Script ( T1202 ): This scenario abuses the use of the Program Compatibility Assistant Service pcalua.exe to execute a file. Persistence Through Scheduled Task ( T1053.005 ): This scenario creates a new scheduled task for persistence using the schtasks utility. Persistence Through Registry Run and RunOnce Keys ( T1547.001 ): This scenario creates an entry under the HKLM\Software\Microsoft\Windows\CurrentVersion\Run registry key to be run at system startup and acquire persistence. Execution – StealerBot Deployment In this stage, the Backdoor Loader is deployed to the system. Then, DLL side-loading is performed. And finally, the unencrypted version of the StealerBot is dropped and saved to disk. 2024-12 SideWinder Backdoor Loader (vsstrace.dll) Sample ( T1105 ): The SideWinder Backdoor Loader (vsstrace.dll) Sample (SHA256: 44ff1117bb0167f85d599236892deede636c358df3d8908582a6ce6a48070bd4) is downloaded to memory and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples. DLL Side-Loading ( T1574.002 ): This scenario leverages a legitimate and trusted executable to load a malicious Dynamic-link Library (DLL). 2025-05 SideWinder StealerBot Unencrypted Sample ( T1105 ): The SideWinder .RTF Sample (SHA256: d9e373aeea5fe0c744f0de94fdd366b5b6da816209ac394cbbda1c64c03b50b1) is saved to disk to test endpoint controls and their ability to prevent the delivery of known malicious samples. Wrap-up In summary, this emulation will evaluate security and incident response processes and support the improvement of your security control posture against the behaviors exhibited by SideWinder. With data generated from continuous testing and use of this assessment template, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat. AttackIQ, the leading provider of Adversarial Exposure Validation (AEV) solutions, is trusted by top organizations worldwide to validate security controls in real time. By emulating real-world adversary behavior, AttackIQ closes the gap between knowing about a vulnerability and understanding its true risk. AttackIQ’s AEV platform aligns with the Continuous Threat Exposure Management (CTEM) framework, enabling a structured, risk-based approach to ongoing security assessment and improvement. The company is committed to supporting its MSSP partners with a Flexible Preactive Partner Program that provides turn-key solutions, empowering them to elevate client security. AttackIQ is passionate about giving back to the cybersecurity community through its free award-winning AttackIQ Academy and founding research partnership with MITRE Center for Threat-Informed Defense. *** This is a Security Bloggers Network syndicated blog from AttackIQ authored by Ayelen Torello . Read the original post at: https://www.attackiq.com/2025/11/13/emulating-sidewinder/
AttackIQ Frequently Asked Questions (FAQ)
When was AttackIQ founded?
AttackIQ was founded in 2013.
Where is AttackIQ's headquarters?
AttackIQ's headquarters is located at 171 Main Street, Los Altos.
What is AttackIQ's latest funding round?
AttackIQ's latest funding round is Series C.
How much did AttackIQ raise?
AttackIQ raised a total of $80.9M.
Who are the investors of AttackIQ?
Investors of AttackIQ include Index Ventures, Titanium Ventures, Salesforce Ventures, Khosla Ventures, Atlantic Bridge Capital and 13 more.
Who are AttackIQ's competitors?
Competitors of AttackIQ include Pentera, SpecterOps, NetSPI, Picus Security, CovertSwarm and 7 more.
Loading...
Compare AttackIQ to Competitors

Cymulate operates within the security validation domain, offering a platform for security validation, tools for breach and attack simulation, continuous red teaming, and exposure analytics to help organizations identify and address vulnerabilities. The solutions challenge and optimize cybersecurity measures across various sectors, including enterprise IT and managed security services. It was founded in 2016 and is based in Tel Aviv, Israel.

CyCognito focuses on exposure management in cybersecurity. The company provides a platform for discovering, testing, and prioritizing security risks, allowing organizations to identify and address vulnerabilities in their attack surface. CyCognito's services are aimed at large enterprises with offerings related to software supply chain security and subsidiary risk monitoring. It was founded in 2017 and is based in Palo Alto, California.

SCYTHE specializes in cybersecurity solutions and focuses on adversarial emulation and enterprise risk assessments. The company offers a BAS+ adversarial emulation platform that enables organizations to conduct realistic enterprise risk assessments and mimic real-world cyber threats. SCYTHE's services include threat analysis, controls validation, and purple teaming, designed to enhance cybersecurity preparedness and response capabilities. It was founded in 2017 and is based in Arlington, Virginia.

Praetorian operates as a cybersecurity company specializing in offensive security services and continuous threat exposure management. It offers a suite of solutions including attack surface management, vulnerability management, breach and attack simulation, and red teaming exercises to identify and remediate exploitable vulnerabilities. It serves various sectors with a focus on providing deep cybersecurity expertise to defend against sophisticated attacks. It was founded in 2010 and is based in Austin, Texas.

Pentera provides Automated Security Validation in the cybersecurity industry. The company has a platform that allows organizations to test the integrity of their cybersecurity layers and identify security exposures. Pentera's services apply to various sectors, focusing on security measures and cyber exposure. It was founded in 2015 and is based in Petah Tikva, Israel.

Bishop Fox provides services in offensive security, including penetration testing, red teaming, and attack surface management, alongside assessments for application, cloud, and network security. The company serves sectors such as technology companies and enterprises with sensitive data and systems. It was founded in 2005 and is based in Tempe, Arizona.
Loading...

