Dragos
Founded Year
2016Stage
Series D - II | AliveTotal Raised
$438.2MValuation
$0000Last Raised
$74M | 2 yrs agoMosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
+6 points in the past 30 days
About Dragos
Dragos offers industrial cybersecurity for operational technology (OT) environments. It offers a platform to provide visibility into industrial control systems (ICS) and OT assets, manage vulnerabilities, and detect and respond to threats. It serves industries, including electric, oil and gas, manufacturing, and more, with solutions tailored to each sector's unique cybersecurity challenges. It was formerly known as Dragos Security Services. It was founded in 2016 and is based in Hanover, Maryland.
Loading...
Dragos's Product Videos


ESPs containing Dragos
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The operational technology (OT) security tools market provides cybersecurity solutions that protect industrial control systems, SCADA systems, and other critical OT infrastructure from cyber threats. These tools offer real-time monitoring, threat detection, asset discovery, and network segmentation specifically designed for industrial environments. Companies in this market serve manufacturing, ene…
Dragos named as Outperformer among 15 other companies, including Microsoft, Cisco, and IBM.
Dragos's Products & Differentiators
The Dragos Platform
The Dragos platform provides a comprehensive security view of the ICS/OT systems. It is a combination of virtual or physical sensors within ICS, software that runs on-prem or in the cloud, and optional managed threat hunting and incident triage services. We provide: •Visibility – into asset inventory, vulnerabilities, & ICS communications • Detection – of threats and anomalous behavior • Response – tools to investigate incidents, collect and analyze forensic information, and run time playbooks to bring issues to speedy resolution
Loading...
Research containing Dragos
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned Dragos in 7 CB Insights research briefs, most recently on Feb 25, 2025.
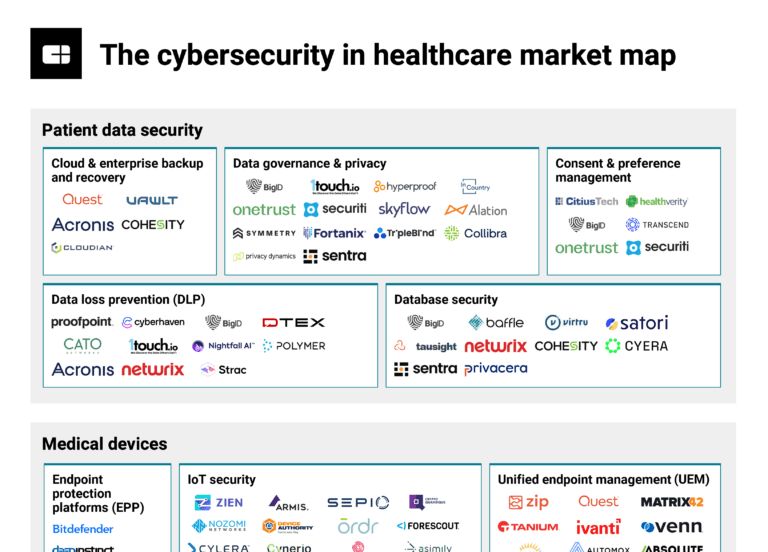
Feb 25, 2025
The cybersecurity in healthcare market map

Feb 20, 2024
The hardware security market map
Aug 16, 2023
The industrial internet of things (IIoT) market map
Jul 28, 2023
The cloud security market mapExpert Collections containing Dragos
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
Dragos is included in 5 Expert Collections, including Unicorns- Billion Dollar Startups.
Unicorns- Billion Dollar Startups
1,309 items
Cybersecurity
11,227 items
These companies protect organizations from digital threats.
Advanced Manufacturing
7,019 items
Companies in the advanced manufacturing tech space, including companies focusing on technologies across R&D, mass production, or sustainability
Advanced Manufacturing 50
50 items
Future of the Factory (2024)
436 items
This collection contains companies in the key markets highlighted in the Future of the Factory 2024 report. Companies are not exclusive to the categories listed.
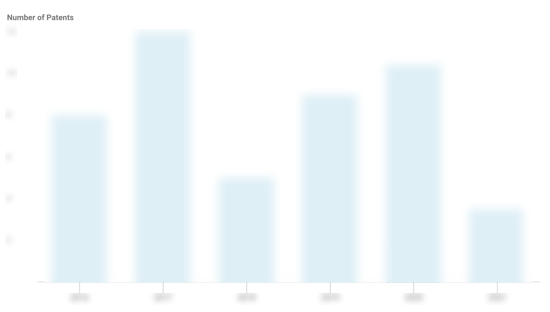
Dragos Patents
Dragos has filed 2 patents.
The 3 most popular patent topics include:
- data management
- business intelligence
- computer network security
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
5/12/2021 | 6/13/2023 | Computer security, Software testing, Computer network security, Windows Server System, Data management | Grant |
Application Date | 5/12/2021 |
|---|---|
Grant Date | 6/13/2023 |
Title | |
Related Topics | Computer security, Software testing, Computer network security, Windows Server System, Data management |
Status | Grant |
Latest Dragos News
Nov 9, 2025
WASHINGTON Oct. 29, 2025 Corsha , the first and only Machine Identity Provider (mIDP) purpose-built to secure machine-to-machine (M2M) communication across operational systems and critical infrastructure, introduces a partnership and new platform integration with Dragos, Inc., a global leader in operational technology (OT) cybersecurity. Together, Corsha and Dragos are transforming how organizations secure industrial systems by combining machine identity and threat detection to give security teams complete visibility, precise control, and a trusted foundation for Zero Trust in OT. As operational networks grow more complex and connected, the stakes for securing them have never been higher. Every new machine, sensor, or autonomous system introduced into production environments expands the attack surface, and too often these devices communicate without authentication or accountability. At the same time, adversaries are leveling up to exploit those unseen connections, using trusted but unverified machine traffic to move laterally and evade detection. Achieving Zero Trust for OT requires more than network visibility or perimeter defenses; it demands continuous verification of every machine and every action. By combining Corsha's automated machine identity and continuous authentication with Dragos' deep industrial threat intelligence, organizations can now ensure every machine communication is identity-verified, and that threats are detected, contained, and remediated before they disrupt operations. "Machine-to-machine communication has become the backbone of modern operational systems, yet it remains one of the least protected layers of the OT environment," said Anusha Iyer, CEO and Founder of Corsha. "By integrating our machine identity platform with Dragos' threat detection platform, we are giving organizations the ability to continuously verify every connection and act on identity-driven intelligence in real time. This partnership brings Zero Trust for OT to life, strengthening resilience, accelerating response in real time, and securing the core of how critical industrial systems connect." "Securing OT environments requires both deep visibility into threats and confidence in every machine connection, and integrating Corsha's machine identity platform with the Dragos Platform gives customers context to act with speed and confidence," said Dan Dorchinsky, VP Public Sector, Dragos Inc "By combining Corsha's machine identity with Dragos's deep industrial monitoring and visibility, asset discovery, risk-based vulnerability management, and threat detection, we are helping organizations strengthen their defenses and operational resilience." The Corsha and Dragos integration unite two complementary layers of OT defense: continuous machine identity from Corsha and advanced threat detection from Dragos. Through a direct integration, the two platforms work together to give organizations comprehensive visibility, trust, and control over their operational environments. Prevent unauthorized and unusually risky machine communications. Dragos provides deep visibility to detect anomalies and threats across ICS/OT networks, while Corsha enables identity-driven microsegmentation and ensures only verified machines can initiate or maintain connections. Together, they help prevent unauthorized machine activity, reducing the risk of lateral movement, ransomware, and supply chain compromise. Strengthen Zero Trust for OT environments. The joint solution delivers deeper Zero Trust coverage by combining Dragos' real-time asset visibility and threat detection with Corsha's dynamic machine identity with policy-based microsegmentation and access controls. This helps organizations move beyond detection to active enforcement of trusted communications, especially for non-human connections. Improve incident response efficiency with automated enforcement. By adding machine identity context to Dragos high-fidelity detections, Corsha enhances intelligence around trusted communications, further streamlining triage and response. Teams gain clearer, more actionable insights that accelerate investigation and response across OT environments. Advance SANS Five ICS Critical Controls with machine identity . Through the Dragos integration, the Corsha mIDP adds machine identity and access control to help meet the Defensible Architecture guidelines within the SANS Five ICS Critical Controls. By continuously verifying and authenticating machine-to-machine communications, the joint solution enforces strict boundaries across industrial networks and builds layered defenses that are resilient, auditable, and aligned with industry best practices. Together Corsha and Dragos enable organizations to achieve Zero Trust for OT by validating every connection, enriching detections with machine-level identity, and dynamically controlling access based on risk. This combined capability helps organizations more quickly identify malicious activity, contain incidents, and maintain safe, continuous operations in the most demanding industrial environments To see the integrated Corsha + Dragos solution in action, sign up for a live demo https://corsha.com/request-a-demo About Corsha Corsha securely connects the operational systems that run our world. As the connections between legacy and modern systems grow, the Corsha Machine Identity Provider (mIDP) makes it easy to securely connect any machine, move data, and automate with confidence. With patented advancements in connection discovery, continuous authentication, and behavioral identity and access for machines, the Corsha mIDP empowers manufacturing, public sector, and critical infrastructure enterprises to overcome security bottlenecks, dramatically lower risk, and accelerate adoption of modern technologies like robotics and physical AI. Corsha is backed by leading venture capital investors including Ten Eleven Ventures, Razor's Edge Ventures, Sinewave Ventures, Booz Allen Ventures, and Cybernetix Ventures. Learn more at www.corsha.com This News is brought to you by Qube Mark , your trusted source for the latest updates and insights in marketing technology. Stay tuned for more groundbreaking innovations in the world of technology.
Dragos Frequently Asked Questions (FAQ)
When was Dragos founded?
Dragos was founded in 2016.
Where is Dragos's headquarters?
Dragos's headquarters is located at 1745 Dorsey Road, Hanover.
What is Dragos's latest funding round?
Dragos's latest funding round is Series D - II.
How much did Dragos raise?
Dragos raised a total of $438.2M.
Who are the investors of Dragos?
Investors of Dragos include WestCap, DataTribe, AllegisCyber Capital, Energy Impact Partners, Schweitzer Engineering Laboratories and 10 more.
Who are Dragos's competitors?
Competitors of Dragos include Nozomi Networks, Claroty, CyberX, Mandiant, RSA Security and 7 more.
What products does Dragos offer?
Dragos's products include The Dragos Platform and 4 more.
Who are Dragos's customers?
Customers of Dragos include Trinity River Authority (TRA).
Loading...
Compare Dragos to Competitors
Barikat Cyber Security provides cybersecurity solutions within the information security sector. The company offers data protection, cloud security, compliance analysis, DevSecOps services, and various security technologies. Barikat Cyber Security serves both public and private sectors, focusing on information protection. It was founded in 2008 and is based in Istanbul, Turkey. Barikat Cyber Security operates as a subsidiary of Barikat Group.
Cerebra is a software products company focused on the design and development of cybersecurity technologies. The company provides products including an enterprise messaging gateway for communication, a multi-factor authentication system, a cybersecurity awareness platform for education, a phishing simulation solution to test employee awareness, a single sign-on platform for access, and compliance monitoring tools for regulatory adherence. It was founded in 2020 and is based in Riyadh, Saudi Arabia.

Sophos provides cybersecurity solutions, including Managed Detection and Response, incident response, endpoint, network, email, and cloud security, aimed at protecting organizations from cyberattacks. The company serves various sectors by offering cybersecurity-as-a-service, security operations platforms, and hybrid solutions that can be managed directly by the organization or supplemented with additional services. It was founded in 1985 and is based in Abingdon, United Kingdom.

McAfee operates in the cybersecurity sector, offering services such as antivirus software, identity theft protection, and online privacy solutions. The company provides features including device security, identity monitoring, credit monitoring, and virtual private network services. McAfee was formerly known as Network Associates. It was founded in 1987 and is based in San Jose, California.

eSentire provides managed detection and response (MDR) services within the cybersecurity domain. The company offers services including threat hunting, incident response, and cyber threat intelligence to protect organizations from cyber threats. eSentire's clientele includes various sectors such as finance, healthcare, and legal industries, which require cybersecurity measures. It was founded in 2001 and is based in Waterloo, Canada.
NanoLock Security focuses on operational technology cybersecurity within the industrial and manufacturing sectors. The company provides a security solution that aims to protect industrial devices, machines, and manufacturing lines from cyber events and human errors. NanoLock's products serve the energy utilities, water utilities, and manufacturing sectors. It was founded in 2016 and is based in Nitzanei Oz, Israel.
Loading...