CrowdStrike
Founded Year
2011Stage
IPO | IPOTotal Raised
$481MDate of IPO
6/12/2019Market Cap
132.95BStock Price
529.78Revenue
$0000About CrowdStrike
CrowdStrike is a cybersecurity company that provides protection for endpoints, cloud workloads, identities, and data. The company offers a platform that includes threat detection, protection and remediation, threat hunting, and observability of vulnerabilities. CrowdStrike's services are aimed at securing areas of enterprise risk and are applicable to various sectors. It was founded in 2011 and is based in Sunnyvale, California.
Loading...
ESPs containing CrowdStrike
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The vulnerability management market helps organizations identify and prioritize vulnerabilities in their IT systems, networks, and applications to reduce the risk of cyberattacks and data breaches. Companies provide insights into potential security gaps with guidance on remediation, often featuring automated security validation, threat intelligence integration, and real-time vulnerability detectio…
CrowdStrike named as Leader among 15 other companies, including Google Cloud, Accenture, and Amazon Web Services.
Loading...
Research containing CrowdStrike
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned CrowdStrike in 6 CB Insights research briefs, most recently on Sep 25, 2025.
Feb 5, 2024
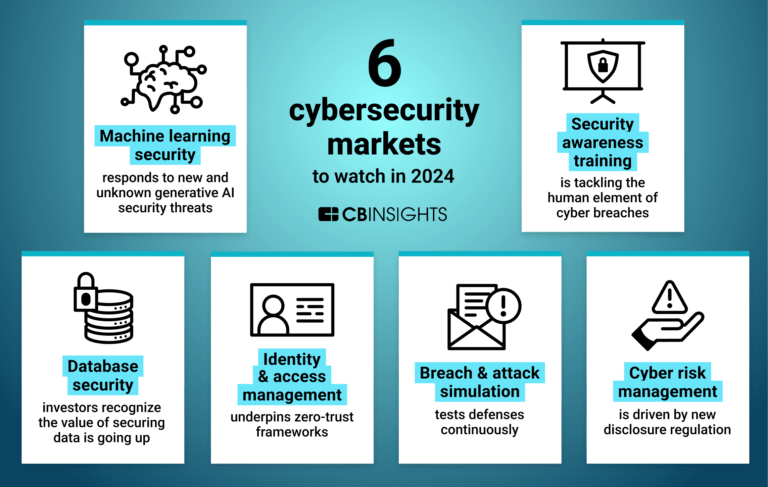
6 cybersecurity markets gaining momentum in 2024
Nov 3, 2023
The endpoint security market map
Jul 28, 2023
The cloud security market mapExpert Collections containing CrowdStrike
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
CrowdStrike is included in 8 Expert Collections, including AI 100 (All Winners 2018-2025).
AI 100 (All Winners 2018-2025)
99 items
Winners of CB Insights' annual AI 100, a list of the 100 most promising AI startups in the world.
Tech IPO Pipeline
286 items
Conference Exhibitors
5,302 items
Cybersecurity
11,390 items
These companies protect organizations from digital threats.
Generative AI
2,951 items
Companies working on generative AI applications and infrastructure.
Artificial Intelligence (AI)
20,894 items
CrowdStrike Patents
CrowdStrike has filed 203 patents.
The 3 most popular patent topics include:
- computer network security
- computer security
- computer security exploits

Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
2/29/2024 | 4/1/2025 | Data management, Configuration files, Web frameworks, Database management systems, Diagrams | Grant |
Application Date | 2/29/2024 |
|---|---|
Grant Date | 4/1/2025 |
Title | |
Related Topics | Data management, Configuration files, Web frameworks, Database management systems, Diagrams |
Status | Grant |
Latest CrowdStrike News
Nov 18, 2025
Research from SoSafe's social engineering team suggests that generative AI tools can help attackers draft convincing phishing messages at least 40% faster than before , which means more attempts and more chances to get through. Once attackers gain a foothold, they are moving through networks faster than ever. CrowdStrike's 2025 Global Threat Report found that the average breakout time — the window between initial compromise and lateral movement through an organization's networks — has dropped to 48 minutes, with the fastest observed intrusion completing in 51 seconds. CrowdStrike's data paints a simple picture: If defenders are still thinking in hours, they are already too late. To match that speed, a new class of AI-driven defenses is emerging to help security teams respond at the tempo of modern attacks. These systems watch streams of content, code and user behavior in real time, surfacing patterns no human team could track alone. At the center of this shift is a simple idea. Cyberattacks now happen faster than humans can detect or respond to, so defense can no longer depend on human speed alone. AI is becoming essential because it can keep up with the pace of modern threats, while humans still guide the nuance, context and judgment it cannot provide. Attacks At Machine Speed Attackers today do not need days to plan. They can spin up campaigns in minutes, often across countries, platforms and languages all at once. Generative AI makes it easy to personalize lures, disguise malicious content and probe for weak spots at scale. A recent incident showed how real and immediate this shift has become. Four days ago, Anthropic announced it disrupted a highly sophisticated AI-led espionage campaign. The AI company said it first detected suspicious activity in mid-September and that it later traced it to a Chinese state-sponsored group running a live cyber-espionage campaign. The group manipulated Claude Code, Anthropic's own frontier model, to automate most of the intrusion workflow — from scanning networks to crafting tailored exploits — while human operators stepped in only for a few critical decisions. Anthropic's disclosure offered a rare look at how machine speed changes not just how attacks begin, but also how widely and quickly they can spread. Attackers no longer move in neat linear steps. Automated tools probe software flaws while human operators test stolen credentials and AI-generated content hits inboxes at the same time. Each layer supports the next, leaving defenders almost no room to pause or verify. And that's exactly the imbalance many security teams are grappling with today. Traditional tools were built for slower, predictable intrusions, not rapid-fire AI campaigns. AI-driven monitoring matters because it gives defenders back what automation has taken away — a few crucial seconds to see, decide and act. “The shrinking window between vulnerability and exploitation has changed the entire game,” said Daniel Shechter, CEO and cofounder of Miggo Security , which offers an AI runtime defense platform for applications. “What used to be reserved for nation-states is now scriptable, scalable and sold on Telegram.” Humans In The AI Loop Companies like Miggo Security and ActiveFence are exploring ways to blend algorithmic power with human judgment. ActiveFence focuses on trust and safety for global platforms, scanning billions of interactions each day across text, image, video and audio in dozens of languages. ActiveFence's work places it at the forefront of combating online abuse and coordinated manipulation. “We recognized early that generative AI would become not only a massive opportunity but also a new frontline in the fight for online security and integrity,” said Noam Schwartz, CEO and cofounder of ActiveFence. “Our mission is to safeguard digital interactions in real time with intelligence-driven guardrails so organizations can confidently deploy AI-powered experiences without compromising safety,” he said. Miggo Security, by contrast, looks inside the software itself. Its platform tracks how applications behave in production, spotting unusual patterns in how services interact rather than relying on static signatures or predefined rules. Shechter explains this philosophy simply: “You cannot defend what you cannot see, and real defense comes from combining how applications behave with predicting the way the attacker will break in , not just how attackers try to break them.” “Detection at machine speed is only valuable if the organization can respond equally fast,” he said. “It is not enough to see the problem. You have to preempt the attack.” Schwartz makes a similar point. “As AI becomes the backbone of both innovation and attack, global policymakers and security leaders must learn from each other, fast. The question isn't whether AI will shape the next generation of threats; it's whether we can shape AI itself to defend against these same threats. The guardrails we build today will decide if AI becomes a weapon or a shield,” he noted. Together, these approaches point to an emerging cybersecurity model where AI and humans work closely together to proactively protect critical data assets. Algorithms handle the volume and the speed. Humans decide what matters and what action to take next. The Expanding Attack Surface As organizations adopt more systems and more AI, the number of places that can be attacked keeps growing. In other words, the attack surface is expanding at a rate most traditional defenses were never designed to manage. Modern applications depend on dozens of small services that constantly interact. Companies rely on cloud platforms, third-party APIs, workplace apps and customer-facing systems distributed across regions. Many are also rolling out AI assistants and agents that can act on instructions, access data and trigger workflows. While these AI assistants are helpful for businesses, they are also helpful for attackers. Bad actors are increasingly trying to exploit the way AI models work by changing prompts or data to make the systems act in harmful ways. This is why runtime visibility — understanding how systems behave moment to moment — is becoming essential. Threats no longer live only in suspicious emails or user posts. They also live in the interactions between services, the way code executes, and the decisions AI models make under pressure. Reclaiming The Balance The future of digital defense will not be defined by speed alone. It will also depend on how well security teams understand what they see and how quickly they act. While AI gives defenders the reach to watch everything at once, only people can weigh the context behind what they see. More organizations are adjusting to that reality, building workflows where machines surface patterns and humans decide how to respond. This is becoming less of an aspiration and more of a requirement. The internet is already too fast and too complex to protect in any other way. So, the teams that learn to pair machine awareness with human clarity will be the ones who stay ahead.
CrowdStrike Frequently Asked Questions (FAQ)
When was CrowdStrike founded?
CrowdStrike was founded in 2011.
Where is CrowdStrike's headquarters?
CrowdStrike's headquarters is located at 150 Mathilda Place, Sunnyvale.
What is CrowdStrike's latest funding round?
CrowdStrike's latest funding round is IPO.
How much did CrowdStrike raise?
CrowdStrike raised a total of $481M.
Who are the investors of CrowdStrike?
Investors of CrowdStrike include Accel, CapitalG, March Capital, General Atlantic, Institutional Venture Partners and 12 more.
Who are CrowdStrike's competitors?
Competitors of CrowdStrike include Red Canary, Goodfire, Cylance, Beryllium Security, TXOne Networks and 7 more.
Loading...
Compare CrowdStrike to Competitors

Sophos provides cybersecurity solutions, including Managed Detection and Response, incident response, endpoint, network, email, and cloud security, aimed at protecting organizations from cyberattacks. The company serves various sectors by offering cybersecurity-as-a-service, security operations platforms, and hybrid solutions that can be managed directly by the organization or supplemented with additional services. It was founded in 1985 and is based in Abingdon, United Kingdom.

McAfee operates in the cybersecurity sector, offering services such as antivirus software, identity theft protection, and online privacy solutions. The company provides features including device security, identity monitoring, credit monitoring, and virtual private network services. McAfee was formerly known as Network Associates. It was founded in 1987 and is based in San Jose, California.

eSentire provides managed detection and response (MDR) services within the cybersecurity domain. The company offers services including threat hunting, incident response, and cyber threat intelligence to protect organizations from cyber threats. eSentire's clientele includes various sectors such as finance, healthcare, and legal industries, which require cybersecurity measures. It was founded in 2001 and is based in Waterloo, Canada.

Bitdefender provides threat prevention, detection, and response solutions across various sectors. The company offers cybersecurity products and services for consumers, small businesses, and enterprises aimed at protecting against digital threats. Bitdefender's offerings include endpoint security, cloud security posture management, and managed security services, supported by AI-powered threat intelligence. It was founded in 2001 and is based in Bucharest, Romania.
Cerebra is a software products company focused on the design and development of cybersecurity technologies. The company provides products including an enterprise messaging gateway for communication, a multi-factor authentication system, a cybersecurity awareness platform for education, a phishing simulation solution to test employee awareness, a single sign-on platform for access, and compliance monitoring tools for regulatory adherence. It was founded in 2020 and is based in Riyadh, Saudi Arabia.
Barikat Cyber Security provides cybersecurity solutions within the information security sector. The company offers data protection, cloud security, compliance analysis, DevSecOps services, and various security technologies. Barikat Cyber Security serves both public and private sectors, focusing on information protection. It was founded in 2008 and is based in Istanbul, Turkey. Barikat Cyber Security operates as a subsidiary of Barikat Group.
Loading...